timestripe encryption
Our lifetime goals are sensitive information, no kidding.
We take security very seriously and responsibly and do everything to make sure that all your data is stored in a private cold place. Our servers are well protected and we use encrypted connections so that no intruders can peek into your private life. But sometimes we feel the need to take it to the next level. Now it is possible.
When you enable encryption in the Settings and enter your password, here's what happens:
On your computer
You
send the data from your keyboard to the Browser.
The Browser
displays the data on the screen and connects to the server.
On the web
The Server
sends the data to the browser via the network.
You press the switch button ONOFF to enable encryption and enter your password:

Nothing has been sent online and the Server hasn’t received any information yet.
When You type in your password the Browser generates a unique encryption key.
The encryption key is encoded in a key picture, an abstract image made up of lines and dots. To generate the picture, the Browser uses your password and a random salt — a sequence of bytes that obscures and protects your password. With different salts, even the same password produces different keys.
 2.2. You download the key picture to your computer.
2.2. You download the key picture to your computer.
 2.1. The Browser generates a key picture using the password and salt.
2.1. The Browser generates a key picture using the password and salt.
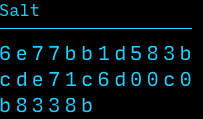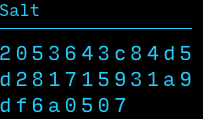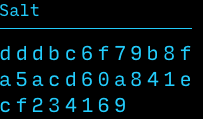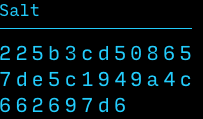
Salt := 32 random bytes
Key := PBKDF2 (Password, Salt)
2.3 Browser stores the key on your computer, so that you don’t need to enter the password every time
There is no way to learn the password from the key, so even if you laptop gets stolen your password will remain secret.
It is also safe to share your key picture, because in order to see your goals one needs to log in with your Facebook or Goggle account.
The Browser sends the salt to the Server, so that the key can be regenerated from your password the next time you log in.
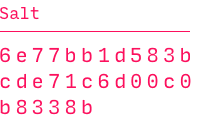 The Server stores stores only the salt, but not your password or key picture, which are never uploaded to the network.
The Server stores stores only the salt, but not your password or key picture, which are never uploaded to the network.
The Salt is totally random and there is no way to learn your password or key from it.
The Browser generates a verification pair and sends it to the Server to be able to verify your password the next time you enter it.
A verification pair consists of two sequences of bytes or, as we call them, ‘texts’. The first is totally random, and the second is the encrypted version of the first.
 4.1 The Browser generates a verification pair
4.1 The Browser generates a verification pair
Text := 32 random bytes
Encrypted Text :=
ENCRYPT (Text, Key)
 4.2 The server uploads the pair to the database
4.2 The server uploads the pair to the database
There is no way to learn the password or the key from the verification pair.
If the encryption is 
The key is fetched from the local storage. If you use a different browser or clear your browser’s cache, the key is generated from the password you enter or from the key picture you select.
 5.1 You add a goal
5.1 You add a goal
 5.2. The Browser encrypts the goal using the key.
5.2. The Browser encrypts the goal using the key.
Salt := 32 random bytes
Encrypted Goal :=
ENCRYPT (Goal, Key, Salt)
To encrypt each goal a new goal salt is generated, and even the same goals produce different encrypted results.
The Browser sends the encrypted goal and the goal salt to the Server, which uploads them to the database.
 The Server gets the encrypted goal and the salt, but not the plain text.
The Server gets the encrypted goal and the salt, but not the plain text.
The Goal Salt is totally random and there is no way to learn the goal or the key from it.
The next time You log in, the Browser tries to obtain the key from the local storage on your computer, and if it is not possible, it asks the Server to send the key salt.
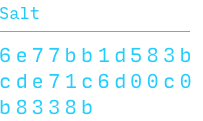 7.1. The Browser receives the salt from the Server and is ready to generate a key.
7.1. The Browser receives the salt from the Server and is ready to generate a key.
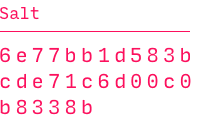
Key := PBKDF2 (Password, Salt)
 7.5. Or you can insert your key picture into the password field.
7.5. Or you can insert your key picture into the password field.
 7.6. The Browser gets the encryption key.
7.6. The Browser gets the encryption key.
 7.7. The Browser receives the verification pair from the Server and checks if the key is correct.
7.7. The Browser receives the verification pair from the Server and checks if the key is correct.

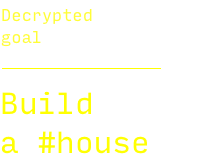
 7.8. The Browser gets encrypted goals from the Server and decrypts them using the key.
7.8 Then the browser get the encrypted goals from the server and using the key it can decrypt your goals
7.8. The Browser gets encrypted goals from the Server and decrypts them using the key.
7.8 Then the browser get the encrypted goals from the server and using the key it can decrypt your goals
Dercrypted Goal :=
DECRYPT(Encrypted Goal,
Key, Salt)
At this moment, the Browser has decrypted goals in the session memory which will be erased when you close the tab.

As you can see, at no moment the server has plain-text goals, and it doesn’t possess complete information required to decrypt them. All sensitive data exists only in your browser until you close the tab.
The information stored on the server is useless without your password or key. So if you forget the password and lose the key, it will make your secrets completely inaccessible to all humankind. It will simply be impossible to recover your goals and, alas, you’ll have to reset them. So please be careful.
FAQ
Whew, that’s a lot!
Yeah, security requires some effort.
You’ve published your algorithm! Now you will be hacked!
Nope. Security through obscurity is not for properly protected systems. Modern encryption algorithms are designed to be impossible to break even if revealed. And peer review helps to make protection even better.
If you find any flaws in our algorithm, please contact us at admin@timestripe.com.
You say it’s impossible, but what if some bad guy simply brute forces my password?
Well, it can happen. But the encryption functions we use ensure that it will take many supercomputers and many years to decrypt your information. This is called ‘cryptographic impossibility’.
This can be dangerous only if the bad guy first takes possession of your Facebook or Google account, or obtains the database from our server, which is highly unlikely.
OK, but what if, say, some three-letter organization asks you to decrypt my goals?
Well, we will be unable to help, even if we really wanted to. Sorry.
2015 2025 timestripe
We will be happy to hear from you. Don’t hesitate to send us your ideas and comments — info@timestripe.com